An Attempt to Build on Dr Grimes Viability of Conspiratorial Beliefs
Got a secret
Can you keep it?
Swear this one you’ll save
Better lock it in your pocket
Taking this one to the grave
If I show you then I know you
Won’t tell what I said
‘Cause two can keep a secret
If one of them is dead?
— The Pierces
Like most folks I enjoy a good conspiracy theory, and sometimes even a bad one. They allow the listener to suspend disbelief and consider for a moment that the social world in which he or she resides is an illusion. This is somewhat similar to the ability to slip into the fictional world of a story or novel, and bears similarity to the Gnostic assertion that the material realm is an entrapping illusion. In fact many very good films are based on the idea that conspiracies are afoot–the Bourne, Mission Impossible, Star Wars, and of course the Matrix series.
In modern societies, however, there are many conspiracy theories peddled as truth that cause real harm to their believers. One recent example from my country is PizzaGate–a ridiculous story based on the notion that a major Presidential candidate was operating a pederasty ring through a Washington DC pizza place–that led to a believer carrying out an armed raid. Another example is the belief that childhood vaccination is a cause of autism, an assertion founded on falsified data. Failure to vaccinate has led to numerous outbreaks of dangerous epidemic diseases in just the last few years. I should note that the longest running conspiracy theories I know of aren’t theories at all because in the minds of their believers they aren’t disprovable. In that sense they are fictitious certainties,
In his 2016 paper “On the Viability of Conspiratorial Beliefs” Dr David Grimes of Oxford University applied probability models to four popular conspiracy theories–NASA moon landing hoax, climate change fakery, vaccination-autism link, and cancer cure conspiracy. His model simulates the probability of a conspiracy being leaked using a Poisson distribution with conspiracy population parameters based on exponential decay, the Gompertz function, and no change. In order to understand Dr Grimes work a little better, I coded his equations in Octave and simulated his parameters, replicating the generalized results displayed in Figure 1 of the paper.

Three graphs showing my calculations, with Figure 1 from Dr Grimes paper in the lower right quadrant
In examining the work I found one point where I wanted to test a variation. The population parameters and probability distribution used in the paper are continuous–the growth models allow for fractions of a conspirator to leak information. I added an integer rounding function to the population parameters. I also decided on a binomial discrete probability function, where the probability of a leak is treated similarly to the probability of a defective part rolling off an assembly line. I also added a parameter that allows for a leak, presumably to the press, to require verification from additional defectors.
To test this formula I decided to test the fake job numbers conspiracy. The idea is that the US Bureau of Labor Statistics was cooking up job numbers in 2012 to assist the reelection campaign of President Obama. A few problems with this are:
- The BLS employs more than 2500 individuals with a broad range of political preferences
- Job figures are also measured by private firms, such as Gallup and ADP, which show different raw numbers but similar trends
- There really isn’t any evidence that the average American voter pays close attention to economic releases
The down side to the discrete formula is that it uses factorial numbers to calculate the binomial coefficient. Numbers greater than 170! are treated as infinite by Octave. To mitigate this, I used a conspiracy population of 100, with an individual chance of leaking at 0.1% per year, and a press requirement of 2 defectors to publish the leak. While it looks like it would be possible to carry out such a conspiracy one time, the chance of the conspiracy being broken in 80 years is 91.49%. If one assumes a single leaker is sufficient, the chance of discovery rises to more than 99.99%. The chance of carrying it out with the involvement of 2500 must be slim indeed.
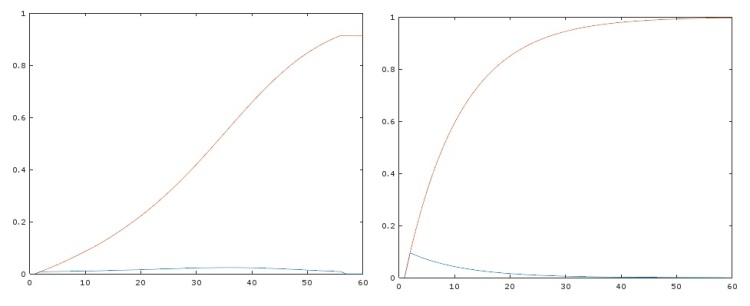
Results from discrete probability analysis of the fake job numbers conspiracy forwarded during the 2012 US Presidential election. On the left, requirement of two leakers, on the right requirement of one leaker.
The m file code for the discrete distribution is below:
function conspViaDisc(decayType, p, N0, numIt)
x = [1:numIt]; % fill x-vector for x-axis values
alpha = 10^-4;
beta = 0.085; % alpha & beta for gompretzian function
te = 40; % mean age of conspirators
lifeExp = 78; % mean life expectancy of conspirators
lambda = log(2)/(lifeExp-te);
N(1) = N0;
a = 1; % Number of leakers needed to break the conspiracyif decayType == “G”
for n = 2:numIt
N(n) = int16(N0*exp(0-lambda*n)); % Gompretzian decay
end
elseif decayType == “E”
for n = 2:numIt
N(n) = int16(N0*exp((alpha/beta)*(1-exp(beta*(te+n))))); % Exponential Decay
end
else
for n = 2:numIt
N(n) = N0; % No Decay
end
endifL(1) = 0.001; % Estimated probability of discovery in timestep 1
cumL(1) = L(1);
for n = 2:numIt
if N(n) >= a
summ = 0;
for m = 1:a
s = m-1;
binCoef = factorial(N(n))/(factorial(s)*factorial(N(n)-s));
summ += binCoef*(p^s)*((1-p)^(N(1)-s));
end
L(n) = (1-summ)*(1-cumL(n-1));
cumL(n) = cumL(n-1) + L(n);
else
L(n) = 0;
cumL(n) = cumL(n-1) + L(n);
end
endN
L
cumL
plot(x,L,x,cumL)
Posted on January 22, 2017, in Uncategorized. Bookmark the permalink. Leave a comment.
Leave a comment
Comments 0